Nillion: Private Data And Secure Computation For All
Mathematician Clive Humby once said “Data is the new oil”, and in five words wildly underestimated true value of the information we generate online. Yet, despite its importance in the digital economy, our personal data remains largely concentrated in the hands of a few megacompanies, who commoditize it without a thought for we who generate it. This is the legacy of “Web2” – an array of ‘free’ applications that actively manipulate and productize the people who use it. Luckily, many builders in Web3 have heard the call to improve the state of affairs, particularly Nillion Network, whose builders herald from giants such as Uber, Coinbase, Google, Nike, and Amazon as well as Web3 institutions like Consensys, Polygon, and Hedera. “We know Web2 has problems around fault tolerance and also problems with privacy” said Nillion’s co-founder Miguel De Vega in an interview with Interchain FM, and Nillion strives to solve these problems.
In this article we will
(1) Introduce you to Nillion’s mission for data privacy
(2) Show you the pillars of their technology stack and
(3) Teach you a bit about cryptography along the way.
Let’s dive in.
An Overview of Nillion
Nillion aims to be the “blind computer” – but what does that mean? It’s a place where data can be safely stored and utilized, while simultaneously preserving the privacy of its owner. It provides a toolbox of different Privacy Enhancing Technologies (PETs) for developers to utilize, and decentralizes their access through a dual network model: the PetNet is a network of node clusters that provide the secure storage and private computation services, and the Nillion blockchain serves as an orchestration layer, matching users with PetNet clusters and facilitating payments.
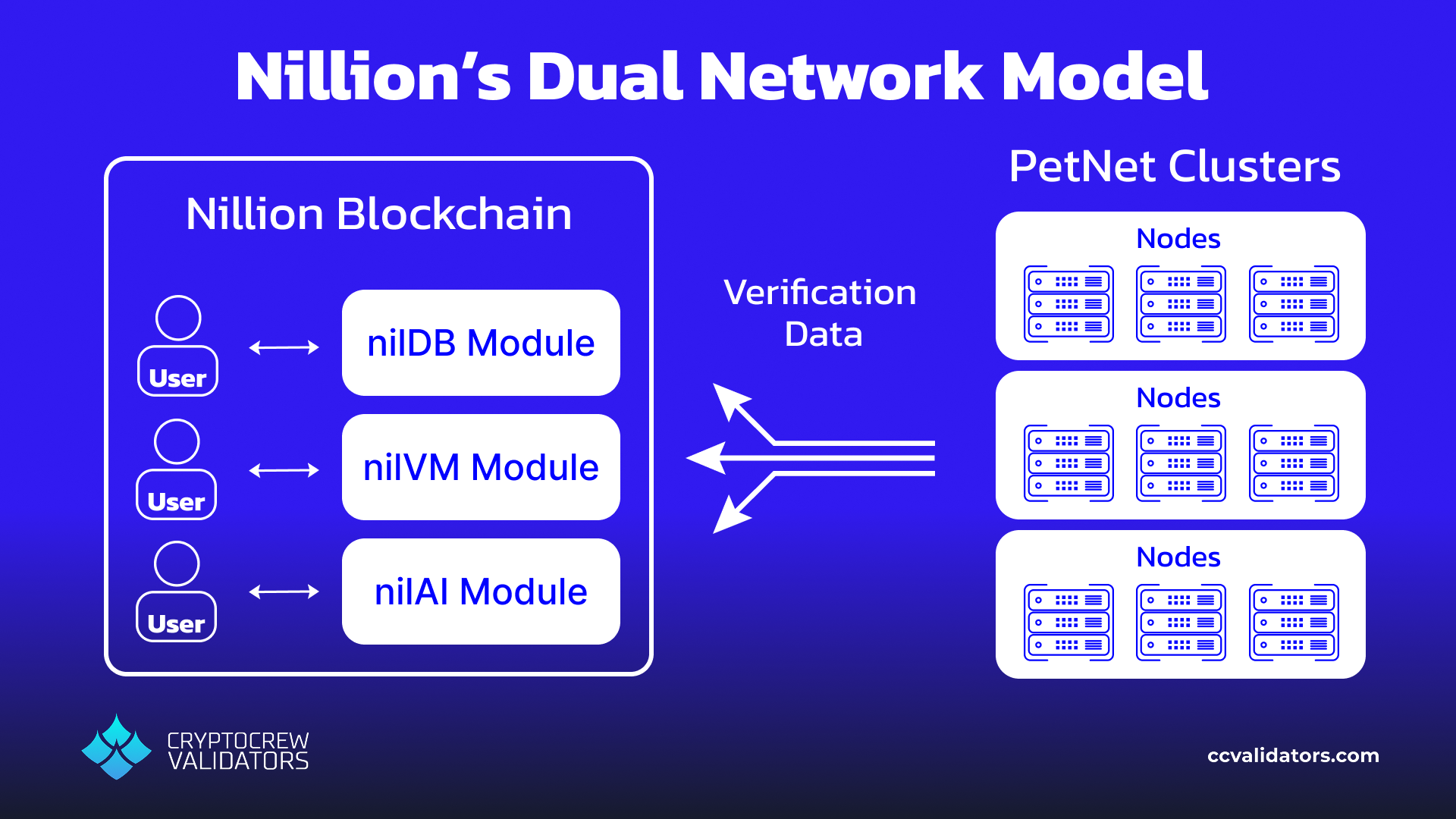
The PetNet nodes are built on three “Blind Modules”: nilDB, nilVM, and nilAI, each of which allows developers access to cryptographic tools suited for different uses. To get a feel for how these components interact, we are going to walk through a few examples from the health care industry of how they might be used and what is possible. Along the way, we will (gently) introduce you to some cool cryptographic fundamentals.
Secure Storage & nilDB Module
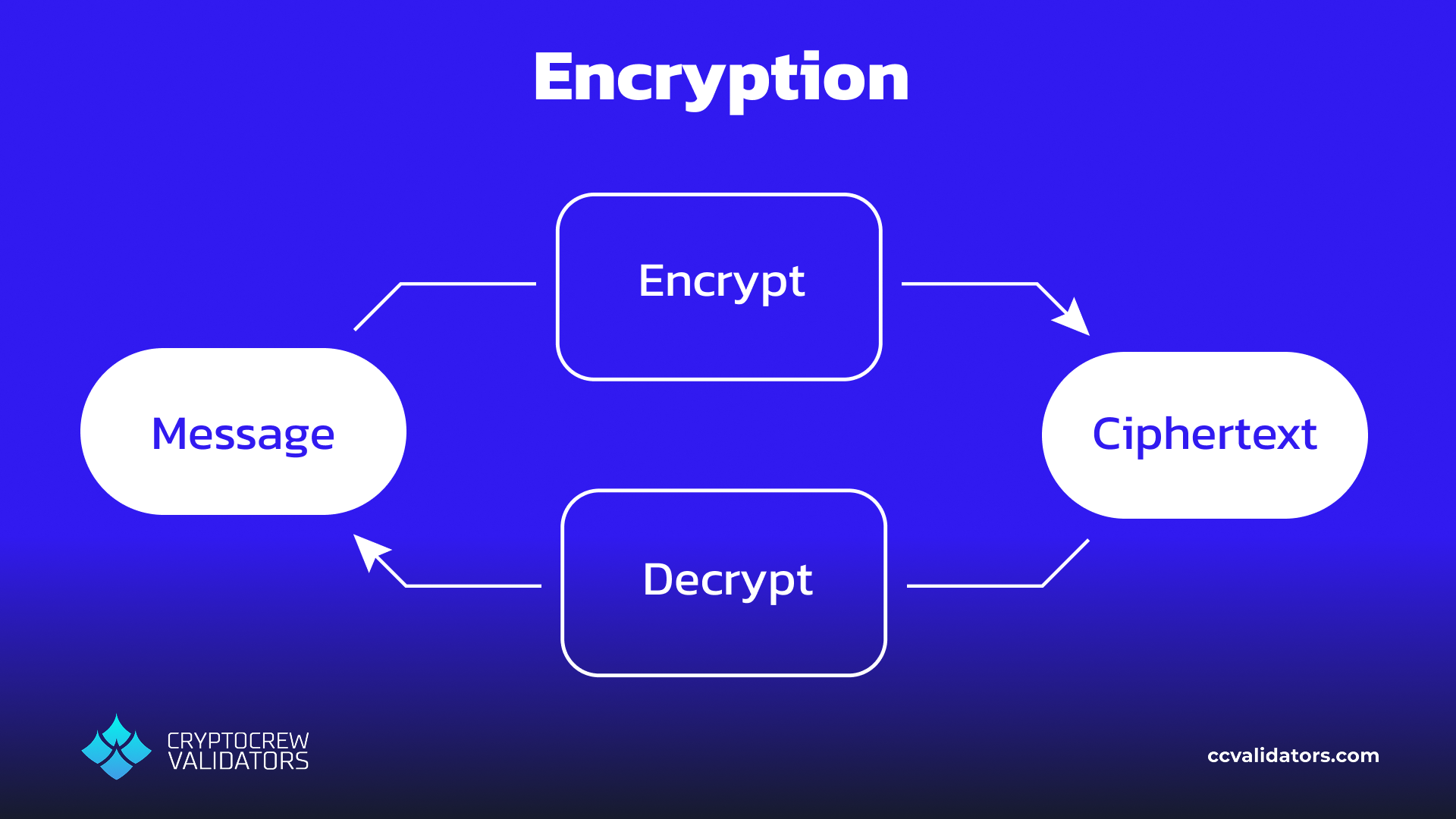
Suppose one day you need to go to see a doctor because you’re unwell. You sit down, and tell the doctor that you’re feeling dizzy and have a headache. The hospital now needs to keep a record of this, and they could opt to use Nillion secure storage solution through SecretVault. Since the information from your appointment is private, it will need to be encrypted when stored. There are many ways to encrypt data, but since we need some of these ideas for later let’s look at a simple Caesar cipher.
Imagine we took the data “Headache, dizziness” and wanted to encrypt it. This data is called a ‘message’ or ‘secret’. An easy way to encrypt this is with a shift key – we simply bump each character by some number of letters. If we shift everything forward by 3 letters, we would get the encrypted message – or ciphertext – “khdgdfkh, glcclqhvv”. Now, if some malicious party gained access to the database, all they could read would be these garbled messages. To decrypt this message, they would need the key, which is to shift all the letters back by 3 characters. You can play with some Caesar ciphers here, but it should be noted these are only used as an example and are not sufficiently secure for modern-day encryption.
Encryption
Even using a higher quality encryption key, we can still do better. The nilDB module also allows users to split their encrypted data into shares and spread these across multiple PetNet nodes, ensuring that no single operator can ever unlock the entirety of the data. Only by combining their shares can the data be revealed. This is made possible by a tool that we’ll come to later.
Private Computation and nilVM Module
Now that our hospital has begun storing its sensitive patient data in an encrypted PetNet cluster, imagine that a researcher comes along and would like to do some analysis on it. The most obvious option is for the hospital to use their key to decrypt all the data, revealing it to researcher. However, this would breach patient confidentiality and in many situations, would be illegal. A far better option is to use a tool from the Nillion nilVM module: Homomorphic encryption (HE).
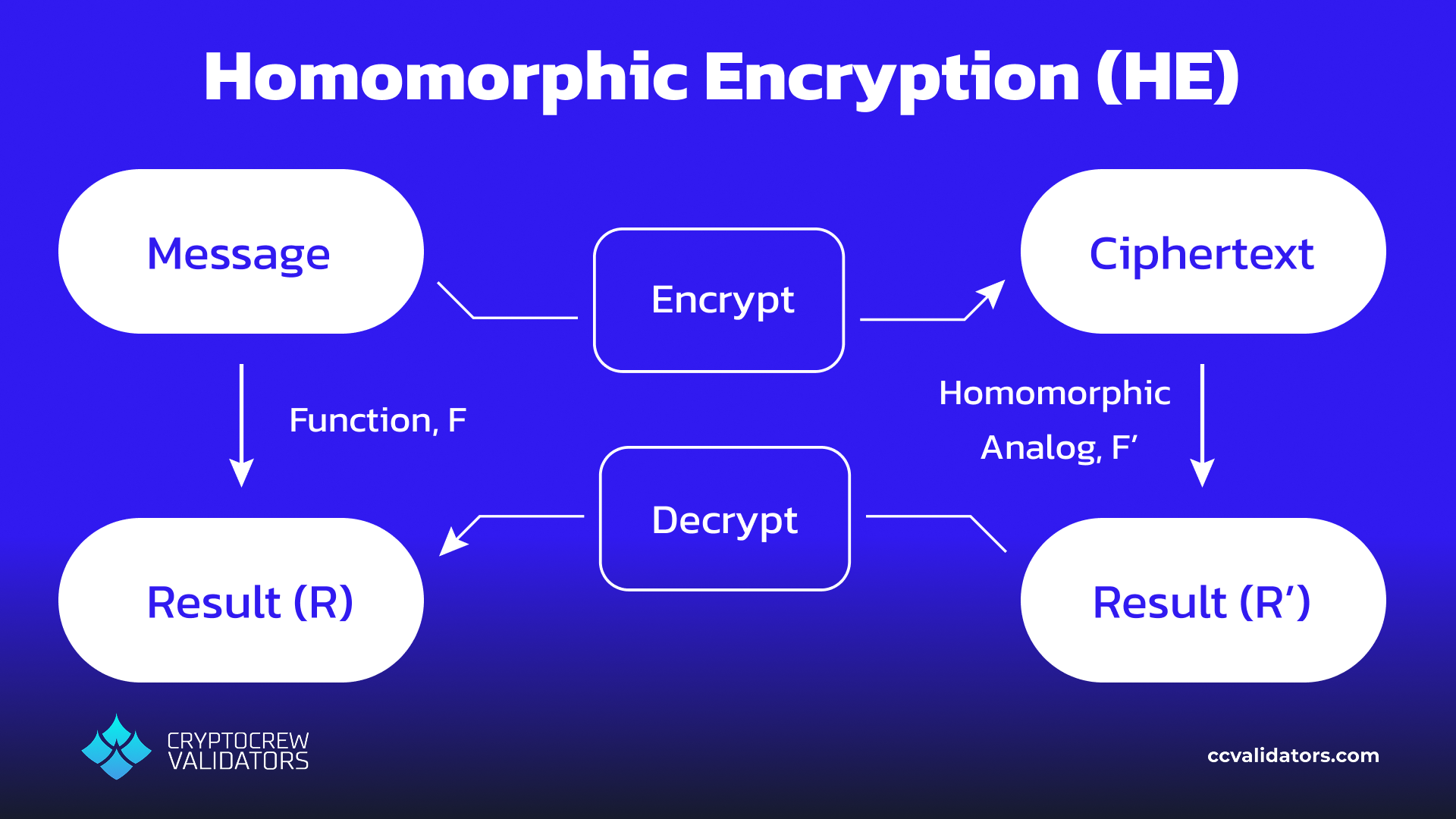
Let’s imagine the researcher wants to compute some result (R), like the average age of patients, or something more complicated. HE allows them to perform their calculations on the data without ever seeing it. This is not intuitive, and it’s made possible by some challenging math, but here’s a very brief overview.
The hospital data has been encrypted, and currently lives in a ciphertext state. The researcher wants to apply some function (F) – like adding the number patients, averaging their age, etc – to the decrypted data to obtain their result (R), but can’t because of confidentiality. Instead, they can apply a related function to the encrypted data, to produce some different result (R’). Here’s what’s wild:
As long as F and F’ are “Homomorphic analogs”, decrypting the result R’ will give the intended result R!
Homomorphic Encryption (HE)
The main takeaway here is that homomorphic encryption lets people perform computations on information without ever having access to it, and there is a mathematical guarantee that their result will be identical to what they would have gotten if they had decrypted the data first. Like I said, wild.
But again, we can go deeper.
Suppose that instead of a single hospital, our researcher wants to perform an analysis across several hospitals. Now, not only should the data be kept secret from the researcher, but each hospital’s data should also be kept secret from the other hospitals!
To enable this use-case, Nillion offers another tool: Secure Multi-Party Computation (MPC). It’s structure is very similar to HE, but with a slight twist. As before, the researcher has some known function (F) that they wish to apply to all data sets, and they need a Secure MPC Protocol which can act on the encrypted versions.
Then, as with HE, this joint computation function will produce a result R’ which can be decrypted to reveal the desired result R!
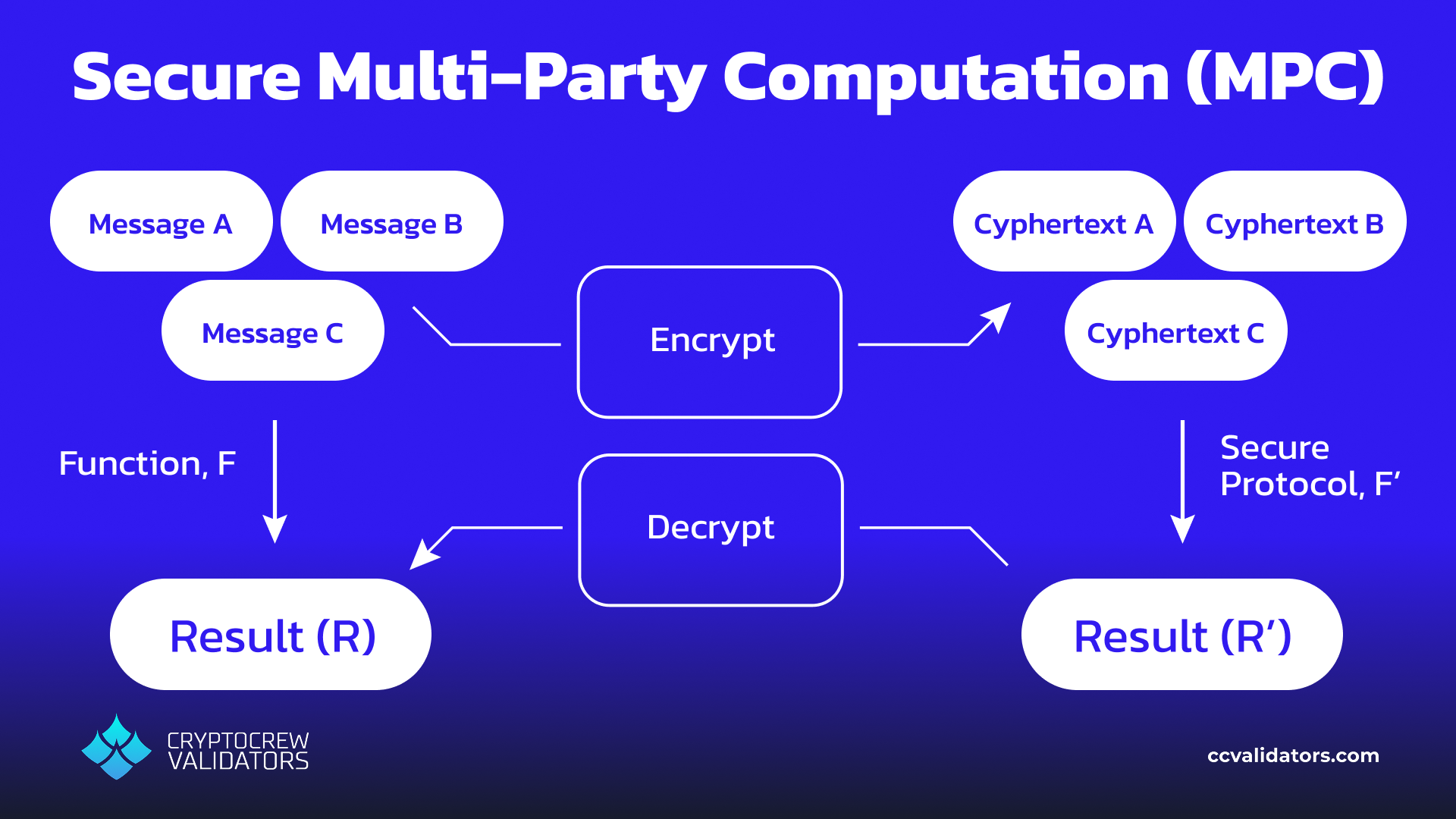
Secure Multi-Party Computation (MPC)
Again, the key takeaway is that MPC allows for an even more complex process to occur which respects the privacy of all parties involved. If this sounds familiar, it’s because MPC is exactly the tool used to reconstruct our distributed encrypted data shares from earlier.
Decentralized AI & nilAI Module
As we near the end of our overview, it’s worth considering one final use case: AI. Suppose our researcher wants to do something much more extensive, like train an AI model on the hospital data. They might be tempted to use either HE or MPC as they did before, but these processes are so complex that this may prove impractical or even impossible. In this case, Nillion SecretLLM offers an additional privacy enhancing tool: computation through a Trusted Enclave Environment (TEE).
Where homomorphic encryption and secure multi-party computation are software-based privacy solutions, a TEE is hardware-based. They reside in special chips which create a computing environment that cannot be accessed (even by its native operating system) and allows computations to be performed privately. The benefits of TEEs is that they allow much faster computations, making them powerful tools for the large amounts of data processing for AI. The tradeoff is that unfortunately, most TEE chips are closed-source and so their utilization introduces additional trust assumptions. Despite this, the outputs of these computations are returned with cryptographic signatures that prove to the user they were performed as expected. As AI training becomes more and more important, retention and control of our data will as well, and Nillion provides tools to move towards this future.
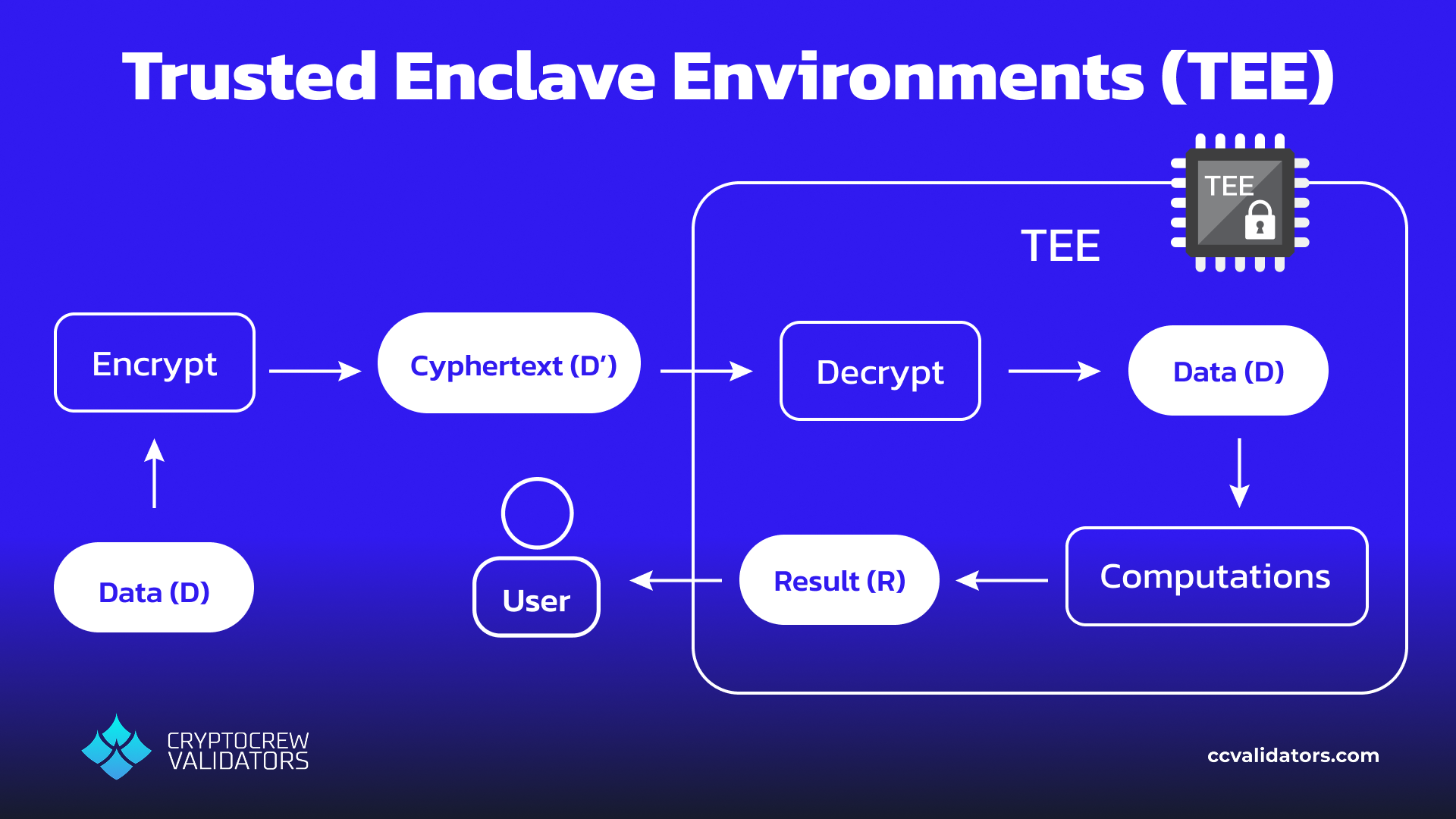
Trusted Enclave Environment (TEE) basic structure
Conclusion
In this article, we have taken you through some healthcare specific example use cases of Nillion’s technology stack, but it’s important to remember that many of these tools are general-purpose. Encrypted messaging, secure document sharing, private Defi, and AI training, inference, and utilization are just a few of the use-cases being explored by ~35 different companies that have partnered with Nillion and are building on their privacy stack.
Web2 privacy solutions are often closed source, proprietary, or rely on other trust assumptions, but Nillion will allow users to access these services through open-source modules facilitated by their Cosmos SDK blockchain. Since each PetNet cluster must reach consensus on the services they provide, Nillion distributes an otherwise centralized service and reduces its trust assumptions.
At CryptoCrew, we are thrilled to be a genesis validator for such an ambitious project and applaud their efforts to bring privacy and control back to the users of web applications. We look forward to a future where cryptography keeps assets and data safe for every human on Earth, and we hope you do too.
Thanks for reading!